Support Proposal 265 on PeakD
Vote for Brianoflondon's Witness KeyChain or HiveSigner
This is a value for value post: see the explanation in the footer.
Happy 4th Birthday Hive!
This post is a bit of a celebration of something which Hive does so much better than all the rest: authentication and accounts.

And its not even close
Hive is the most perfect authentication system on the web. Nothing else around today has anything like these complete features in one, open, package.
It is open and completely open source
It is permissionless
No single entity can control it
It has a self sustaining viable business model
It doesn't require physical hardware but can use it
It is portable
It works on mobile and desktop
Multiple apps and services which overlap
No single point of failure
Methods to recover from and mitigate a lost or leaked private key without losing everything
All of this is going on in the background whenever you sign in on any site using Hive Keychain in your browser, Hive Authentication Services via a QR code or HiveSigner's web based service. Or even PeakLock on PeakD.
The only way I think I can make this obvious to a non technical audience is to explain the process of logging on to websites and how that is different with Hive.
How Does Login In Work?

Not on Hive
Username: Password:
In order to understand what is so revolutionary and important about Hive, you have to understand what is so broken on the old web.
Username: and Password: are the bane of everybody's life. If you're not using a password manager at this point, there is no way anything is secure. If you can remember a password which you've used on the open web, chances are it isn't secure enough. If you can't remember it you're either going to click the "I've forgotten my password" button and then you get an email.
2FA
Because Username and Password are so bad at this point, they've added a patchwork of sticky tape to improve it a bit. SMS messages (horrible and useless because your phone number gets hijacked to get around this.). 2FA with a code from something like Google Authenticator: OK till your child drops your phone in the toilette and for some reason your backup doesn't seem to bring back your codes. Then you'll have to figure out how to get back into whatever service you had there.
Passkeys are a bit better
There's a new shiny thing in the world of logging on. These are called Passkeys and both Google and Apple love them because essentially, if you start using them, you'll end up tying yourself to either your Apple ID or your Google ID. You can use Passkeys with a third party Password Manager like 1Password or Bitwarden.
If you want to delve into this deeper, Steve Gibson on Security Now explains Passkeys well here.
The Problem is always secrets
But fundamentally there is still a problem: the website or service must know or remember something about you. An e-mail address, a username, and your password (or what's called a "hash" of your password.
If using 2FA there is also another secret key which matches a secret key in your 2 factor authenticator app. For Passkeys there is another different public key which matches the secret key in your Passkey.
Any of these things which have to be held by a third party represents a security risk: either that the website will lose control over them or you will lose the device holding them.
How is this different on Hive?
Login on @v4vapp
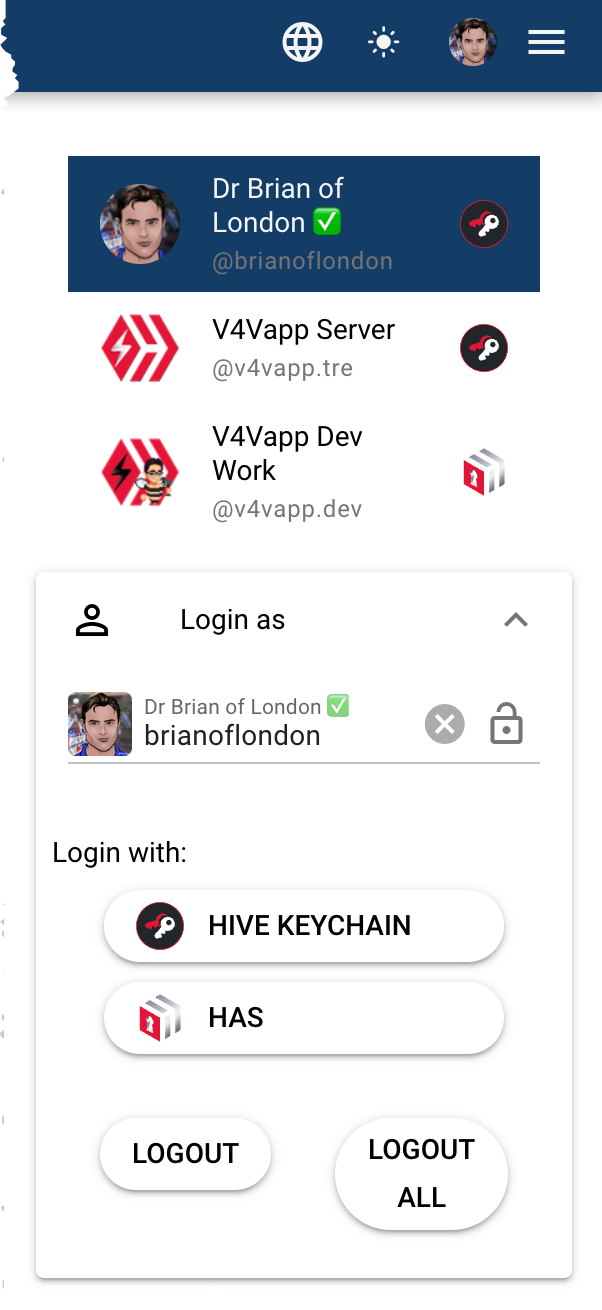
The best way to see how Hive is different and better than EVERYTHING else is by me explaining how I've implemented Hive login and authentication on my own v4v.app web app. You can see the login options when you click on the "hamburger menu" three bars on the top right.
Options
The first thing you see is NO PASSWORD. There's just your username which is your Hive Username. Something you can all remember and TYPE without help.
Under that I have two login options (and really there's a third which I really should add).
- Hive Keychain - the app and the desktop plugin
- Hive Authentication Service (HAS)
- Hivesigner (I haven't added this yet).
Update: I have now realised why I never implemented Hivesigner: as has been pointed out to me by @arcange and others, I don't like the idea of storing keys on a web service. I don't like the architecture of Hivesigner and both Hive Keychain and HAS are much preferred.
What do they all have in common?
The common feature with all these ways to log in on Hive are that THESE apps and services hold your PRIVATE Key for you. In effect they are your Passkey for Hive. But there are three of them and they're open source. That means they all do a different version of the same job and, if you have the skills, you can dig in and review how they work!
Authentication flow on V4V.app
I'll try to explain the authentication flow I use on v4v.app:
On a machine with Hive Keychain as a Browser Plugin
- 1 You enter your Hive name in the Login as box.
- 2 As a safety check the v4v.app web front end retrieves your avatar and your User Profile name directly from Hive. This is important because it helps you double check you've put in your name correctly.
- 3 You click the "Hive Keychain" button.
- 4 Your web browser generates a unique code and sends a request like this to my back end:
curl -X 'GET' \
'https://api.v4v.app/auth/brianoflondon?clientId=e9acb371-779c-4d9c-9b1d-954a767607fc' \
-H 'accept: application/json'
- 5 A call is sent to my public API server asking for a login challenge and something like the following comes back:
{
"challenge": "minimum tackle erase brianoflondon 1711008963.260501 e9acb371-779c-4d9c-9b1d-954a767607fc"
}
- The first three words are random words from the same dictionary used by Bitcoin for generating keys. I'll explain why I use these words later.
- Next is your Hive Username (I'm using
brianoflondonin my example throughout). - A Unix Timestamp
- A unique code which was generated by the client (your web browser) and sent in step 4
- 6 v4v.app tells your browser to open the Hive Keychain browser plugin and show you this screen.
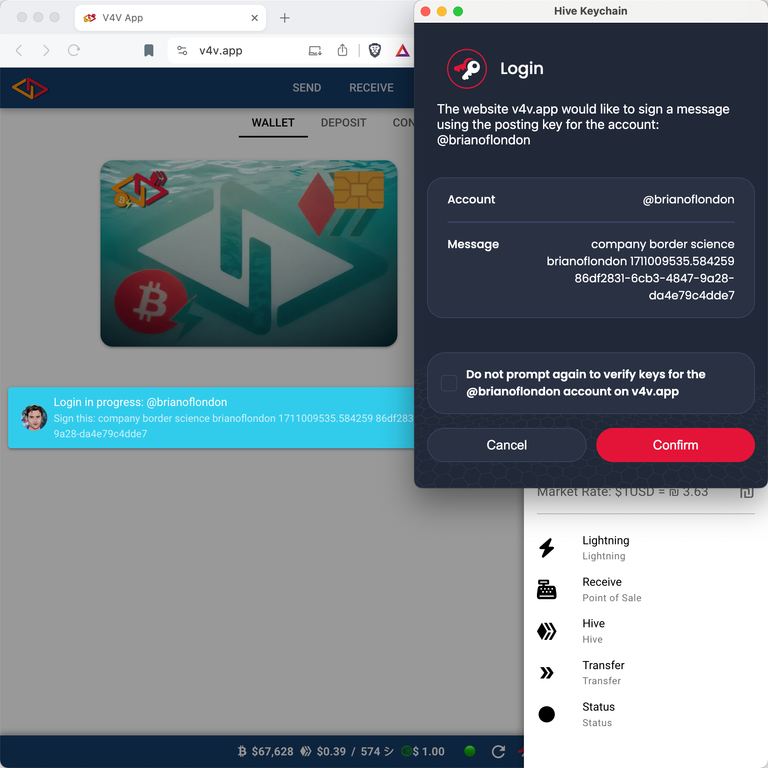
Let's break this down because something magical is happening here.
The cyan box is a message from my website to you telling you you're going to sign a message with the words "company border science brianoflondon" and then some numbers.
Hive Keychain pops up and shows you a message which starts with those exact same words and the numbers. I don't expect you to check the numbers, but the four words (3 random and one your Hive name) you can easily verify by eye.
Keychain says "The website v4v.app would like you to sign a message using the posting key for the account @brianoflondon". All of this makes sense.
7 If you hit "Confirm" the following happens:
- The Hive Keychain software, running inside your browser plugin, uses your Private Posting Key (one of the 4 private keys which control your Hive account) to "cryptographically sign" that message above and return this to the web application still within your browser.
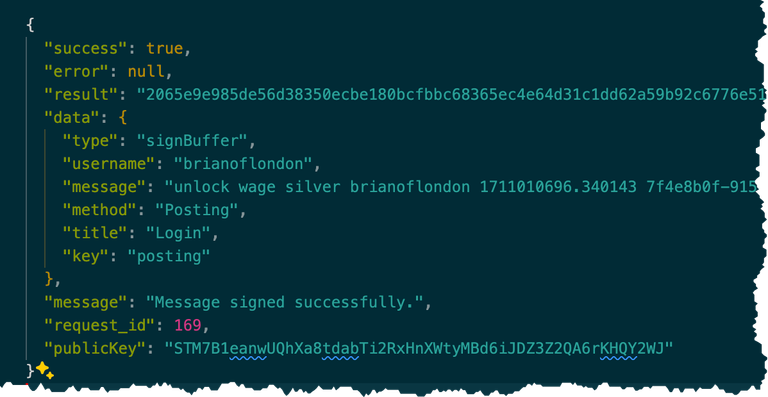
Let's just point out some of the stuff in here.
It has a
result. That's the cryptographic signature which uses your HivePrivate Posting Keycombined with the message to generate this string of letters and numbers.It has the
usernamewhich again isbrianoflondonIt has the
messagewhich in this case is different from above because it's very hard for me to screen shot the whole process in one go :-)Very importantly: it gives the
Public Keyfor this user which matches thePrivate Keywhich was used to sign the message.8 This signed message is actually all my web page needs to know you've authenticated, but there are another couple of steps. This signed information is sent on to the API server which originally generated the challenge message right at the start.
That API server then takes in this message and does a full cryptographic check on the signature. It also does something extra: it checks that the
publicKeyin the signature actually matches thepublicKeywhich is declared on the Hive Blockchain. You can check this yourself: got to https://hive.ausbit.dev/@brianoflondon and if you look down the page you'll find a section called "Authorities", under that is Posting and under that you can find my public key:
STM7B1eanwUQhXa8tdabTi2RxHnXWtyMBd6iJDZ3Z2QA6rKHQY2WJ
- 9 If all of this matches up my API responds in the same way that a normal site would if it got a password match. It issues a
tokento your browser which has a limited lifetime and which the browser can use, going forward, to identify itself as having the permission to read your account information.
Once all of this has happend, which involved typing your username and only 2 clicks for you, that's when you'll see your sats balance and a spray of confetti!
Public Key on Hive
This is something worth highlighting here. Because Hive has its own source of truth about public and private key pairs, this extra check of being able to look directly on the Hive chain to confirm identity is very important.
And because Hive is a distributed blockchain, nobody can specifically say we no longer want @brianoflondon's keys on our chain. Well it could be done: but you'd have to convince 17 out of the top 20 witnesses to simultaneously agree to develop, deploy and then run a new, special version of Hive which specifically decided to remove me! Good luck with that project.
Hive Authentication Service HAS
I'm not going to go step by step through the HAS system because it's mostly the same as above but it's different in very interesting ways and @arcange has just released a new app to help use it. Just like Hive Keychain, it stores your keys securely but unlike Hive Keychain it is much simpler and just does authentication.
There are some good reasons why you might want this. Keychain has become quite complex, a simpler app which is used less and just for one purpose may represent a more secure way of storing your keys, perhaps for high value accounts.
Within the method of working that I've built, Hive Authentication Service (HAS) is also hugely important because it works on a same device log in. If you use v4v.app on a mobile, if you ask for HAS log in you'll get a QR code. You can photograph that with another device, but on a mobile, if you tap it, you'll get taken to either your Hive Keychain or Arcange's HiveAuth app and can sign the message there.
Technical note on HAS
For those of you still following along on the technical details, HAS works slightly differently from the Hive Keychain browser plug in. Because it is a completely separate app, it uses it's own infrastructure to open up a completely different communication channel to your device. This so-called "side channel" is actually a very good thing.
Your HAS signing app once again makes the signature without revealing your private key but it sends it back to my website through this side channel. Once my website gets it, it passes it on to my API back end in the same way as with Hive Keychain.
The others
Web 2.0 with passwords and usernames and e-mail look recovery, patched up with 2FA and all the rest is a mess and will continue to be hacked and attacked for years to come.
Nostr and Bitcoin Maxis
I'm going to mention something which the Bitcoin Maxi crowd developing Nostr like to talk about. They have something akin to our public/private key infrastructure but with a few missing critical elements.
They have a browser plugin (getalby.com) which can play a similar role to Hive Keychain, but on Nostr you only have one Public/Private Key pair. If you make a mistake and post your Private key or it leaks from a third party service, your entire identity is toast. There is now way to revoke and replace your key. We have this on Hive.
The only way to build up any trust in a public/private key pair is to use it posting on Nostr, but because there is no central storage of any messages, it's very hard to point to anything which helps you build a reputation. Nostr is a very basic and poorly thought out system which has huge structural problems.
Bluesky
I haven't looked deeply into the attempts to decentralise this but as always in any probject founded by big venture capital money or a billionaire, they'll struggle with the decentralisation which Hive achieved on the our day of creation with the fork from the old chain.
SQRL
Actually there is one other system which I think is a close run thing for the best. That's something SQRL made by Steve Gibson (whose podcast I quoted above). He spent years working on this protocol and in operation it looks a bit like HAS, but it doesn't require any third party service and it doesn't have a store of public keys. But nobody is using it today and it's pretty much dead in the water.
Any debate?
Am I wrong? Let me know, obviously the best place to tell me is in the comments on Hive.
The Future
We still have a lot of work to do making this easier for users. Lots of us are working on that. But we have an astonishing foundation here on Hive and I don't want any of you, even if you can't follow the technicals, to think that Hive is standing still and not improving.

Value for Value
For the last few months while building @v4vapp I was generously supported by the DHF. Going forward I have a much more modest support which covers direct server costs and a little of my time.
If you appreciate the work I do on and around Hive, you can express this directly: upvoting posts on Hive is great. Also consider a direct donation (there's a Tip button on Hive or a Lightning Address) on all my posts.


Support Proposal 265 on PeakD
Support Proposal 265 with Hivesigner
Support Proposal 265 on Ecency
Vote for Brianoflondon's Witness KeyChain or HiveSigner



