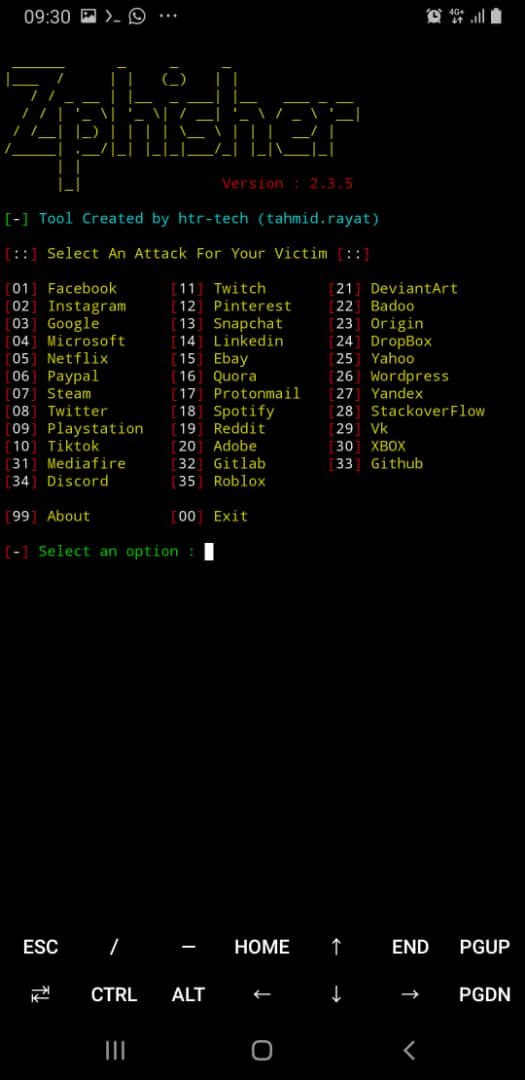
Have you ever wondered how people get to clone all these social media or website logins page?, I remember when I was asked this question I told my facilitator then that they would have to create another site like all these social networks to get people login details not knowing there are tools that can easily generate all this login page template to get people passwords and login.

Screenshot taken by Me
I have once tried creating a phishing link for Facebook just for educational purposes and it looks real, now I see why people easily fall victim to scams of phishing attacks. Zphisher is a really powerful tool that when it gets to the wrong hand a lot of havoc or breaches can be made except an elite that easily differentiates between the real and fake one. I got to know about this tool the day we were engaging in penetration testing, we tried using several tools to test a lab work and vulnerability we then discussed what causes this vulnerability and how this vulnerability is being made.
There are several other tools aside from Zphisher that can be used to cause phishing attacks or cyber attacks on an individual, which is why the unknown needs to be aware. Most of all these tools were created for ethical reasons but hackers find it easy to clone this program in other to use it for their selfish reasons. There are 2 major reasons hacker engage themself in cyber crimes, for money and selfish reasons. I remember reading a history of how people were able to breach a site and steal everyone's login details for personal reasons, no one still knows what is happening now, but majorly hackers work for money.
Zphisher can be cloned on Kali Linux or our Android using Termux. I tried using this on Termux to practice but I have still yet to clone it on my Kali Linux because I have to use it for now, all I just wanted to do was to know how this tool works in cases of emergencies of a breach or vulnerability we can know how to attend to situations or threat like this. I tried using it on my Android.
Screenshot taken by Me
Termux is an open-source Linux terminal for Android. We can use Termux to code Python or run some basic commands. Using Termux on the phone kind of looks interesting. Zphisher was my first engagement on Termux after full installation and Setup of the Termux.
I have never used Zphisher to perform any illicit act, and I am sure I won't use it to perform this but the Zphisher phishing pages look so real. When the person logs into the page, we get to see the individual passwords.
In conclusion, when attempting to log in to any links or social networks sent to us by anyone or an official we must be observant of the source of the link because every one of your login details when input into the wrong phishing pages can easily the breached. This is why most social networks now engage in Two-factor authentication (2FA)
Thank you for Reading My Post
For Educational Purpose Only
Posted Using INLEO