
Original Image Source - Modified by @saydie - Fonts used are Open Source
Hello everyone! @saydie here and this will be my entry for the Newbies Task 3 of the Newbies Initiative that will be focused on various guidelines that we need to know if we one day find ourselves unable to log in our Hive account and realized that we been hacked and how can we recover it. I will also discuss the Hive keys and the possible reasons we are hacked so that we can avoid them.

Hive Keys
Upon the creation of your Hive, you will be given 5 different keys which contains a series of alphanumeric code which only you have an access and was unique for every account. The keys were used for every Hive transaction that we perform in the blockchain in order to make sure that they were authorized only by the user of the account and no one else.
| Keys | Description |
|---|---|
| Memo | Was used to encrypt and decrypt private messages that are sent on the Hive blockchain. |
| Posting | This key was used for social networking actions, like posting, commenting and voting. This key has a limited set of permissions and it is not able to be used for monetary actions. |
| Active | Has additional permissions for more sensitive monetary-related actions, like transferring and exchanging tokens. When performing a wallet related action, you may be prompted to authenticate with your Active key. |
| Owner | The most powerful key because it can change any key of an account, including the owner key. Ideally it is meant to be stored offline, and only used to recover a compromised account. |
| Master | Was required to edit other keys and has additional permissions for account recovery. |
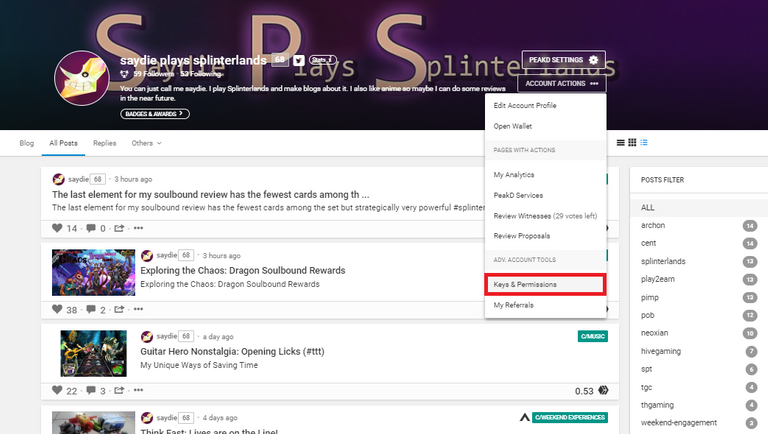
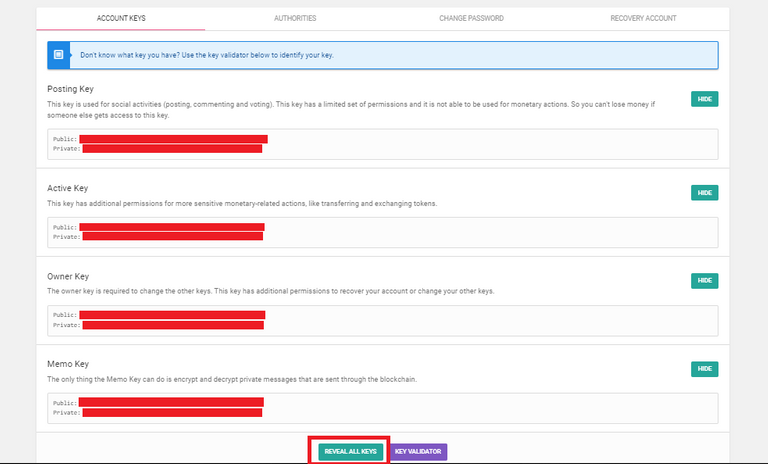
There are various ways to find your keys and as for this post, I will be using Peakd by going to the Account Actions and choosing the Keys and Permissions and you will be transferred to the Account Keys page. Click on the Reveal All Keys and enter your Master Password to see them.
 |  |
Tips For Securing Keys
Unlike passwords from social media platform, we can't retrieve account keys so make sure you have copies of your keys.
Copy them on paper or store them on devices with no Internet access such as Flash Drive.
You should only enter your Active Key into apps which you trust because anyone with access to this key can take your tokens.
Hive Keychain
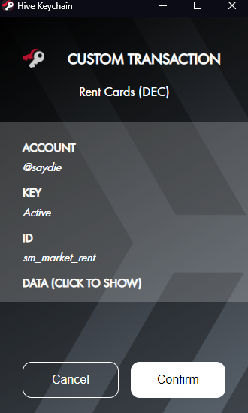
Hive Keychain is a browser extension for Hive blockchain that allows users to securely log in and access different Hive applications without needing to give away your keys as it only signs transactions. It also made the transaction easier as you do not need to type they keys every time that you need to authorize a transaction. You can download the extension here. Hive Keychain also has application for mobile device available for Apple and Android.

Causes For Account Being Hacked
- Phishingis the most common hacking technique. These are messages that is made to look like it came from an actual organization or person which will tell you to click a link or open a file.
- Key Loggeris a software that when downloaded into your computer everything that you type on the computer and allows them to collect all the actions that you do and your keys.
- Viruses and Trojansmalicious software programs that will send your information to the hacker when installed.
To avoid being hacked, we should be careful of the sites that we visit and that they were the official site. Better to Bookmark them so you do not need to type all the time and make a mistake. We should also be careful on the software that we installed and always keep an updated Anti-virus to make sure that no virus enter our devices.

Minimizing Damage
We can never be sure that we will never be hacked. After all were just humans and are bound to make mistakes so at least, we can do some precautionary measures to minimize the lost of the tokens on our account as we try to retrieve the account.
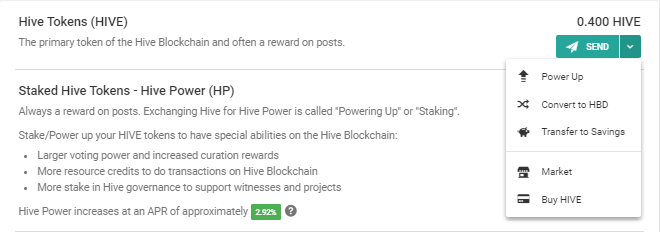
- Hive Power Up
By powering up your hive, not only that it increases your vote value when upvoting other authors, it also allows you to lock your hive and can only withdraw 1/13th of the of your Hive every week while also earning 2.92% APR.
- Transfer HBD to Savings
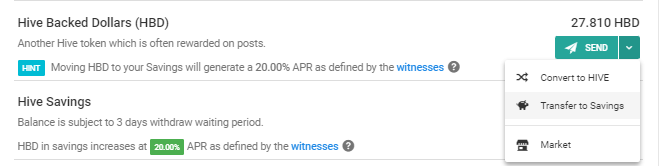
Not only that moving to savings allows you to earn 20% interest for your HBD, it also keeps your HBD locked and will take for 3 days before it can be withdrawn.
- Have A Backup Account
In case that we were hacked, having a backup account to send our liquid Hive and HBD will prevent them to be taken away since they were on a separate account. As for me, the accounts that I have were created for playing Splinterlands and aside for my main one that I use for blogging, the rest were only used for gaming purpose, so it has less interactions with the blockchain meaning less use of the keys. It can also be used as Recovery Account when hacked.

What to do When Accounts are Compromised
Due to the principles behind Hive, recovery of a forgotten password or keys cannot be done as it was not stored on database unlike on social media sites but in case that your Hive account was hacked or lost, there are still some ways to retrieve them on Hive blockchain even if they keys were replaced by setting up a Recovery Account. It is an account that you trust will help you retrieve your keys and will be notified within 24 from when you make the request and would also required your old keys for the process. As long as it in within the first 30 days since your account was compromised there is a strong chance that you can still get the account.
Changing Recovery Account
- For this example, we will also be using PeakD and go to the account actions. Among the options, click on the Keys & Permissions.

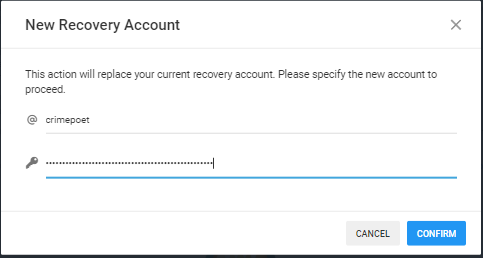
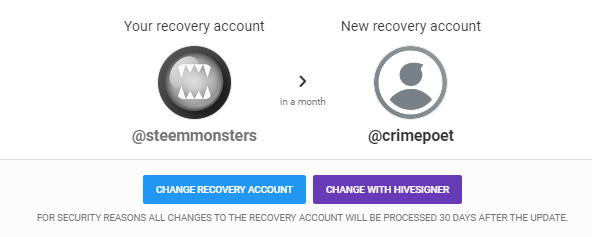
- Instead of going to the Account Keys, you will go to Recovery Account and click on the Change Recovery Account. You can see at my screenshot that my recovery account was currently set to steemmonsters which was a curation account and can be trusted with account recovery.
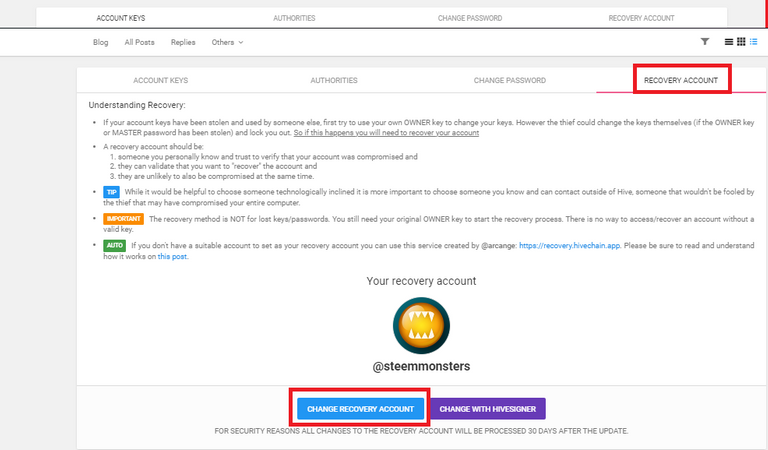
- A pop- up window will appear and will require you to insert the username of the recovery account together with your Owner Key. I have change mine from steemmonsters from my alternate account @crimepoet which is I solely use to play Splinterlands. It will take 30 days for the change to take effect.
| column1 | column2 |
|---|---|
 |  |

Conclusion
To keep our Hive accounts secure, it is important to know the extent of the permissions each of our Keys have and when to use them. We should also only use trusted sites to avoid being hacked. Bookmarking them would be the ideal thing to avoid Phishing sites. It is also important to have a Recovery account so that in case your account was compromised, you can still retrieve your account but make sure that you only have trusted accounts for your Recovery account.
Thank you for reading my post and see you at the next task!
Credits
Screenshots used were from my account using Peakd and Hive keychain.
The Dividers with the Hive logo in this post were created by @thepeakstudio and if you like them you can use them for free, the Hive logo is property of https://hive.io and Keycahin logo is a property of Hive Keycahin.



