HELLO HIVE.
My content this evening is in response to Task 3 of the @newbies-hive Initiative discussing Hive-Keys, Account Recovery and How I identify trustees in Recovery of Account.

Image designed by #projectmamag
To the best of my understanding of the topic through the tutorial on #Discord and the tutorial materials provided on #hive, I will do justice to the topic in question, I hope you learn from it and provide necessary correction where necessary.
"It's proper Netiquette to protect data with passwords. NetworkEtiquette.net”
― David Chiles
Keys/Passwords are a necessity to safeguard our data, else hackers will have free-flow access to our account. So the need for the different Keys with each serving specific purpose and level of strength, therefore safekeeping our keys/passwords properly is of great importance so that a wrong person does not gain access to it.
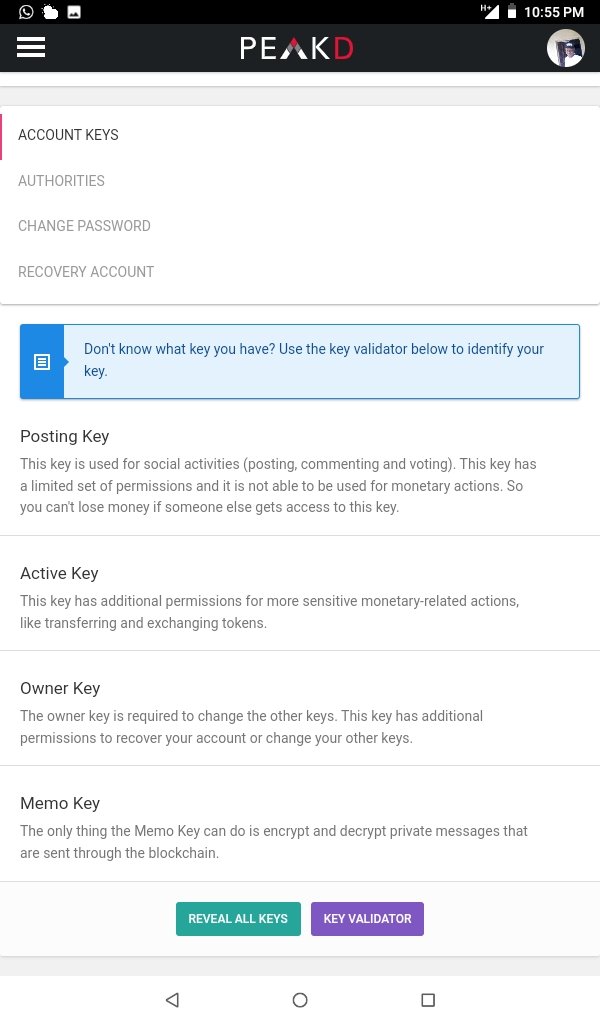
- Posting Key :- The major purpose of this key is for Posting. Editing, Commenting, Re-blogging and Editing in the hive block chain. It also grant us loggin access, thou it use is not really for trivial things, it is still best kept in a safe place.
- Active Key :- This key is very very important, this is because it is the key that anchor financial related dealing on hive Blockchain, examples of such transaction the key is used for are Purchasing and Transferring of Tokens, Powering Up and Down. Conversion of Hive to Hbd or Hbd to Hive. This key should be kept confidential else one loses all the asset that has been amassed over time.
- Owner Key :- It the key used in the recovery and to generate of other keys in the case of misplacement or forgetting. It is a very important key because with it other keys can be accessed.
- Memo Key :- This key is used for sending encrypted or coded messages which can only be read by the receiver or any other authorized perosn. It is the least used of all the keys.
Master Key :- The uniqueness of this key is that aside the fact that it can virtually do all what the Owner Key can do (generating other keys and account recovery), unlike other keys, - Master Keys can only be found in the mail forwarded to our mailbox through the dap we registered with. It is also referred to as Recovery key.
The above listed keys are very important so the need to keep them confidential and inaccessible to just anyone. To do this we can devixe diverse places where we can access them in time if need but far from the reach of intruders. It is this keys that protect our assets and in the recovery of our account should Incase our account got exposed.
- Hardcopy :- Writing out our keys in a jotyer and keeping it with our personal bio-data in our rooms, I would not encourage printing it at a computer centre because this can get our keys exposed.
- Backup in our Mailbox :- This is another way to keep our keys safe, we can creat a draft in our mailbox box and safe all our keys there in, so in the case we changed our phone or it gets lost, we can easily access our Keys back once we logged in to our mail with the new phone.
- Cloud Storage :- Our Keys can also be stored on the net, should there be a demage to our belongings at home, we can get the keys back from the cloud.
- Keeping with Family or Friends :- We can also keep our key safe with a trusted family member (wife, husband, children, siblings) or Friends. We just give them a call when we need the keys, they are only a call away.
**It is very important we keep our keys in multiple places, this implies we have multiple backups should in case one of such safety-link is tampered with.**
Click on the three dotted line which is beside "Setting" on ur profile , then click the option "Keys and Permission" from he window that pops up, chose "Recovery Password", a list will come up stroll downward you will come by the opetion "Account Trustee, you can now change the trustee to anyone of your choice. The !aster key so needed to change a Trustee Account for Recovery, but to recover an account that was hacked both you and your trustee has a role to play to gain back access to such account
Greetings from @seunny






