TL;DR:
"An Avalanche-based lending protocol Nereus Finance is the latest victim of a smart contract exploit as the hacker walks away with a net $371K worth of USD Coin (USDC)" [Mansata, S. $371K Worth USDC Stolen in Avalanche Smart Contract Exploit. (Accessed September 8, 2022)].
Details Surrounding the Avalanche Nereus Finance Exploit
Using very crafty tactics, "USD Coin (USDC) worth $371,000 was siphoned off from Nereus Finance through a smart contract exploit, which blockchain cybersecurity firm Certik caught on Tuesday" [Khatri, A. Avalanche-Based Protocol Loses $371K In Flash Loan Attack. (Accessed September 8, 2022)].
The exploit was first reported by CertiK, a blockchain cybersecurity firm on September 6. The firm indicated that the attack impacted liquidity pools on Nereus relating to decentralized exchange Trader Joe and automated market maker Curve Finance. CertiK also claimed that the underlying protocols themselves were impacted. However, Curve Finance quickly cleared that up by responding, “maybe you meant ‘assets impacted,’ not ‘protocols impacted’. Only @nereusfinance and its assets seem impacted.”
[Mansata, supra].
It should be noted that thereafter, Peckshield, Inc., a blockchain security firm, likewise reported the exploit:
On Wednesday, Nereus Finance released a detailed post-mortem of the incident explaining an 'exploiter' was able to deploy a custom smart contract that utilized a $51 million flash loan from Aave to artificially manipulate the Avalanche (AVAX)/USDC Trader Joe LP (JLP) pool price for a single block. As a result, the anonymous hacker was able to mint 998,000 worth of Nereus’ native token NXUSD against $508,000 worth of collateral. They then swapped this capital into different assets via various liquidity pools and managed to walk away with a net profit of $371,406 once the flash loan was returned.
[Katte, S. Avalanche flash loan exploit sees $371K in USDC stolen. (Accessed September 8, 2022)].
"The Nereus team also acted swiftly by notifying law enforcement, bringing in security professionals, and putting together a mitigation strategy. They also liquidated and suspended the abused JLP market. Furthermore, the team used funds from its own treasury to pay off the bad debt in order to eliminate all risk potential toward user funds" [Khatri, supra].
The detailed 'post-mortem' published by Nereus Finance provides us with just how this crafty exploiter pulled off this theft in a single blockchain block, to wit:
- Call Flash loan of 51,000,000 USDC in AAVE v3
- Swap 280,000 USDC => 14,735 WAVAX in the wAVAX/USDC Joe pool
- Add liquidity 260,000 USDC and 13,401 WAVAX to Joe pool (resulting in the acquisition of 0.04533097793130507 JLP token).
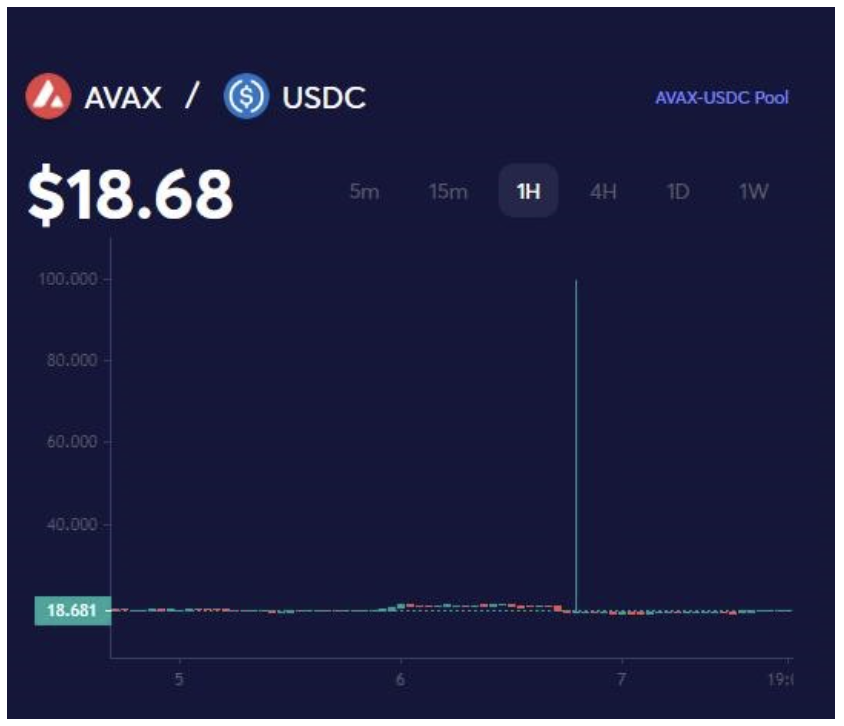
- Swap the remaining 50,460,000 USDC => 505,213 WAVAX in Joe pool, pushing the equivalent pool price up to ~$98 per WAVAX.
- Call borrow function in NXUSD market and deposit 0.04533097793130507JLP, and borrow 998,000 NXUSD from market. [Collateral value now calculated value of ~0.0453JLP = $1,330M USD; when real market value was ~$500K USD]
- Swap 506,547 WAVAX (505,213 + (14,735–13,401)) => 50,426,896 USDC in Joe pool
- Swap 998,000 NXUSD => 955,678 avCRV in NXUSD Factory 3crv pool
- Swap 955,678 avCRV => 977,269 USDC.e in 3crv pool.
- Swap 977,269 USDC.e => (173,238 + 796,772) 970,010 USDC.
- Repay flash loan 51,025,500 USDC to AAVE v3.
Outcome for Exploiter: (970,010 + 50,426,896) — 51,025,500 = 371,406 USDC profit.
[Zeus Nereus. Post-Mortem — Flash-Loan Exploit in single NXUSD Market. (Accessed September 8, 2022)].
This post-mortem likewise explains the protocol defect that permitted the exploiter to accomplish the task.
We recently launched one of our newest collateral types, supporting AVAX/USDC Trader Joe LP tokens. However, there was a missed step in the price calculation resulting in the opportunity to be exploited.
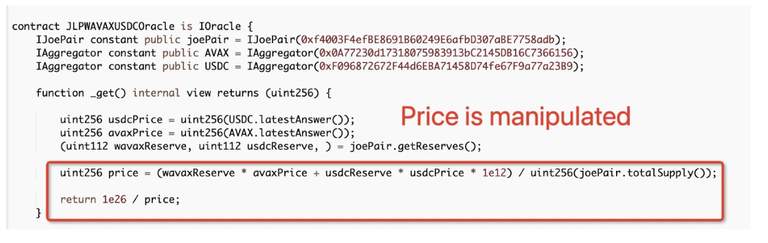
The price calculation was based on the current wAvaxReserve price, usdcReserve price, and totalSupply taken on-chain from the TraderJoe Pool directly without any time weighted average price mechanism implemented in order to prevent potential single block manipulation.
Thanks to @PeckShield for this imageLP price = (wavaxReserve * avaxPrice + usdcReserve * usdcPrice) / totalSupply
As you can see wavaxReserve, usdcReserve, and totalSupply were susceptible to price manipulation due to lack of TWAP calculation. This is shown here in the manipulated pool price chart:
[Id].
"Nereus is also confident the same exploit won’t be possible a second time, as the team will be amending its 'audit and security practices in order to ensure these types of events do not occur in the future'. The Nereus team is trying to identify the hacker and track the funds and has offered a 20% bonus to the White Hats for the refund. However, so far there has been no response" [Coincu. Nereus Finance On Avalanche Process Exploited Flashloan $371,000 Stolen. (Accessed September 8, 2022).
Final Thoughts
"Despite this recent flash loan exploit and several other notable incidents throughout the year, CertiK’s August 2022 Monthly Skynet Alerts Report, released on Sept. 2, claims there has been a notable decrease in these types of attacks. Compared to the previous month, August saw a drop of 95% in flash loan attacks, only resulting in a total loss of $745,244, the second lowest this year" [Katte, supra].
Posted Using LeoFinance Beta

.png)
.png)
.png)